New-SSHSession doesn't recognize PuTTY's key format (unfortunately neither the Gallery nor the project page mention this, but I found it in a PowerShellMagazine article). You need the private key in the OpenSSH format. You can convert the private key with PuTTYgen: Click File → Load private key. SSH keys provide a more secure way of logging into a virtual private server with SSH than using a password alone. With SSH keys, users can log into a server without a password.
Block font for mac. Public key authentication allows you to access a server via SSH without password. Here are two methods to copy the public ssh key to the server.
I believe you understand the basic SSH concept. Your Linux server has ssh enabled. You have generated ssh keys on your personal computer. Now you want to upload your public key to the authorized keys of the server so that you can access it without typing your account password all the time.
Nitro pdf professional v6 2.0 44 x86 and x64 keygen. This quick tutorial shows you two methods to add a public SSH key to the server.
Requirements
Before you see that, let’s be clear about what you should already have:
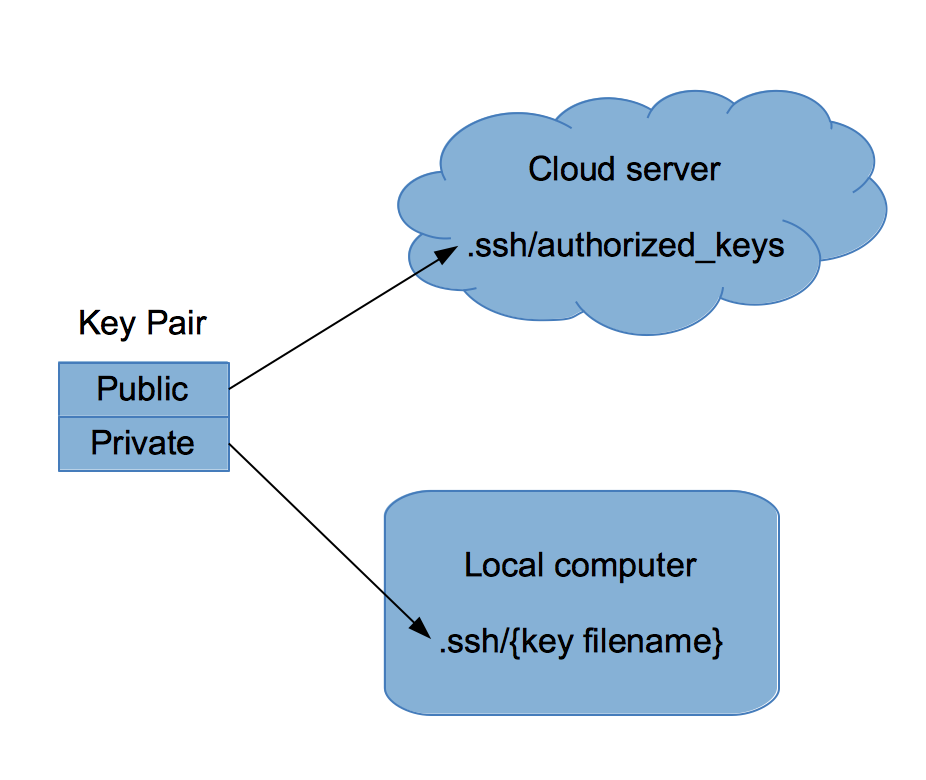
- Your destination server should have ssh enabled
- You should have generated public and private ssh keys (just use the command ssh-keygen -t rsa)
- You should have a user account and password on the server. Even root account will do.
- You should know the IP address of the server
Now that you have made sure of the above three requirements, let’s see how to use public key authentication.
The authentication is per user base so the public key goes in the intended user’s home.
Method 1: Automatically copy the ssh key to server
The first method is where the end user copies its personal computer’s public key to the list of the authorized keys on the remote server.
Here, I assume that you were able to log in to the remote server using ssh user_name@ip_of_server. It asks for your account’s password and you enter the server.
If you add your public key to the server, you should be able to log in without typing the password all the time.
OpenSSH provides a handy tool call called ssh-copy-id for copying ssh public keys to remote systems. It even creates required directories and files.
As I mentioned earlier, you should know the username and password to the server you want to access via public key authentication.
When prompted, enter the password for your user account at the remote server. Your public key should be copied at the appropriate folder on the remote server automatically.
I have used ~/.ssh/id_rsa.pub because that is the default location for the public ssh key. If you have it at some other location, you should use that in the above command.
Method 2: Manually copy the public ssh key to the server
The first method had the action on the user side. Let’s say that you are the sysadmin and your server doesn’t allow SSH login via password. The only way to access the server is using SSH public key authentication.
In such a case, you can ask the end user to provide her/his public key. Now what you can do is to create .ssh/authorized_keys directory and then copy the public key here.
Let me show the steps.
Ssh To Server With Private Key
Step 1: Get the public key
Ask the end user to provide the public key by typing the following command:
It will show a long random string starting with ssh-rsa:

You can get this text via email or messaging tools. Normally, it shouldn’t be a problem.
Step 2: Create ssh directory in the user’s home directory (as a sysadmin)

Keep in mind that you have to create these new directories and files in the end user’s home directory, not your own (root/sysadmin).
Now open this /home/user_name/.ssh/authorized_keys file with a text editor like Vim and add the public key of the user here:
Save and close the file. It’s almost ready.
Step 3: Set appropriate permission to the file
Having appropriate file permission on the ssh file is very important otherwise you’ll see errors like Permission denied (publickey).
First, make sure to set the correct file permissions:
Ssh To Server With Private Key Generator
You created those file with either root or your own admin accounts for some other user. You need to change the ownership to the user:
Ssh To Server With Private Keys

Now that it’s done, you can ask the end user to log in to the server.
Ssh With Private Key Mac
Do let me know if you face any issues or if you have any suggestion on this topic.
Become a Member for FREE
Join the conversation.
